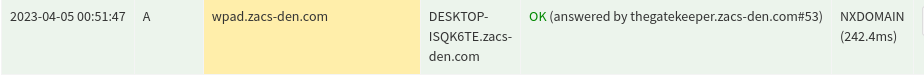
First post in a while I’m aware, but I just had a very interesting thing on my network pop-up. I was browsing queries in my pi-hole for the first time in a while, and I noticed a very strange DNS request coming my brother’s desktop: “wpad.zacs-den.com”. I KNEW that I did not have a device with the name wpad, nor did I have a subdomain by that name. I started to panic, as I thought his computer was possibly hacked, or a intruder had accessed my network. Either way I knew I had to get to the bottom of it.
After looking a little closer, I noticed that each DNS request made for this mystery host came back as an NXDOMAIN. This was very relieving to see as it meant that what ever this wpad thing was not a device on my network, nor was it a malicious subdomain. However, I was still concerned about it as it appeared that it may have been trying to resolve the query outside of my LAN. Since I had reached the end of the evidence that I had available to me, I turned to Google to finally solve this mystery.
The answer I received not only put my mind at ease but also reminded me of why I ditched Windows altogether. Apparently, WPAD is a protocol that tries to automatically detect and and configure proxy settings. Almost every OS has the protocol disabled by default as it can be vulnerable to MitM attacks. Windows however, has this potentially dangerous setting enabled by default. I do not understand why that is but I got him to turn off auto proxy configuration, making my network slightly safer.
UPDATE: It seems Windows wants me to hate it even more. Last night I noticed that my brothers computer was still making requests to wpad.zacs-den.com. I had blacklisted that domain just in case changing that setting did not work, but I still didn’t want it making those requests on my network. So after some more digging I found that the fix is to add an entry to the hosts file that points any WPAD query to 255.255.255.255. I have not seen any queries recently, so fingers crossed it’s resolved now.